DevOps is a proven method for accelerating the Time to Market and the quality of delivery in the application development world. However, the security aspect is not natively included in the approach. Today, the stakes around security are increasing. The DevOps chain can be optimised to take this critical aspect into account.
Definition
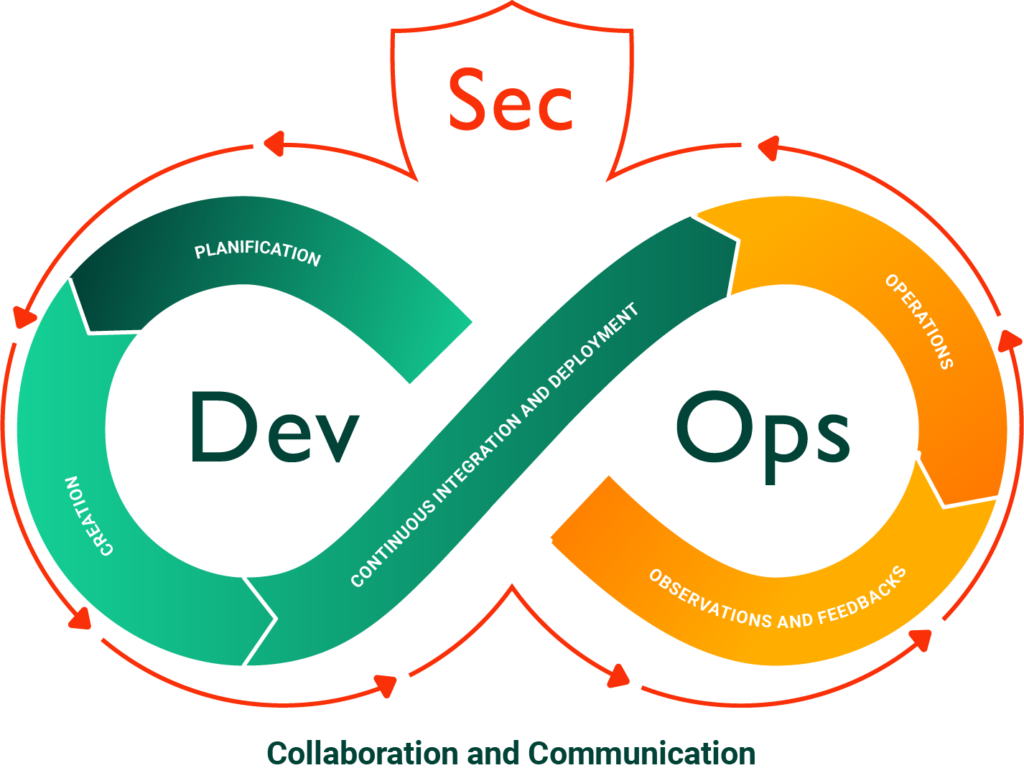
The idea of DevSecOps is to propose an answer to the constant increase security threats to software (Phishing, Ransomware, DDOS attacks, etc.), by placing security at the heart of DevOps processes. Now that the Dev and Ops teams have learned to work together through DevOps, they can now add the burden of security! DevSecOps and then the integration of security into the software development lifecycle, becoming a shared responsibility of the teams.
DevSecOps takes shape in a number of ways. First and foremost, teams need to be trained in security issues and software vulnerabilities. Then, a monitoring process can be put in place. The main activity of DevSecOps is to integrate vulnerability detection processes into the automation of the DevOps cycle, as well as in the best practices for the more manual phases.
The application of DevSecOps in the development cycle
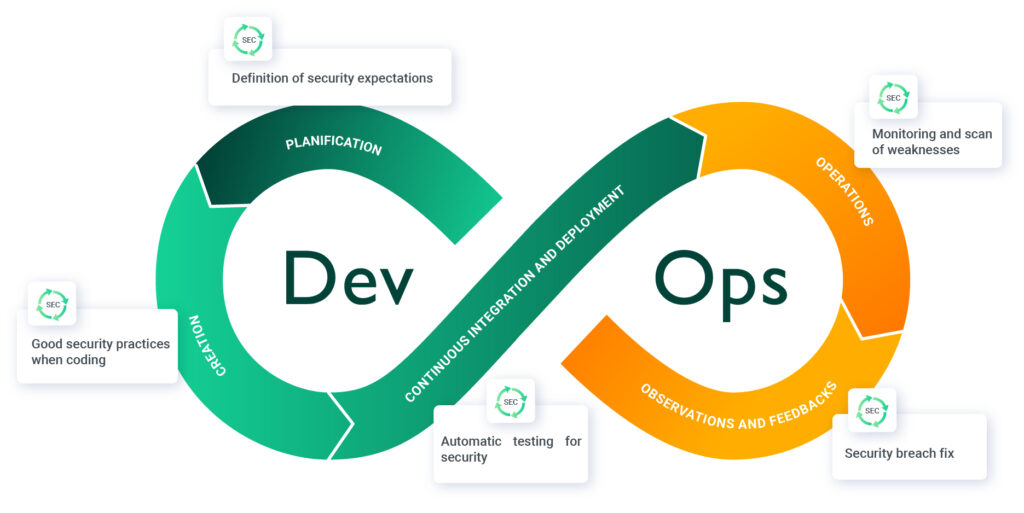
The consideration of security starts at the planning stage where the security requirements are defined. The development teams are made aware of this, and certain developments are devoted to securing the application itself, when all the code must avoid vulnerabilities. The code phase then includes these good development practices for the creation of secure code as early as possible. At this level, the teams themselves check their work against the security issues. Then, the automated CI/CD phase scans the code for vulnerabilities before deployment to production. Since threats can adapt faster than remedies, even if the code is secure at the time of deployment, the exploitation phase must maintain vulnerability monitoring via scanning mechanisms on the application in dynamic operation. Finally, as flaws are often unavoidable, it is advisable to be able to react as quickly as possible in order to pass the correction into the next development cycle, via ITSM tools in particular.
The advantage of DevSecOps is to plan and integrate the detection and treatment of vulnerabilities into each cycle to avoid the urgency of resolving the detection of a flaw. On the one hand, vulnerabilities become less numerous due to a quality/security approach that enables them to be anticipated, and on the other hand, the detection and resolution process is already in place to close these vulnerabilities. Security management becomes more serene, and here again, collaboration between the Dev and Ops teams is essential.
The main steps in implementing a DevSecOps approach are as follows :
- Automating security scans to cover the different attack surfaces
- Planning of vulnerability management
- Integration of security into the DevOps chain
Optimising DevSecOps
The ultimate goal of DevSecOps is proactivity. Teams can be directly allocated to security to find flaws before they are detected by the outside world. Internal ‘hackers’ who work to detect flaws before anyone else so that they are resolved before they are actually discovered. And in terms of proactivity, artificial intelligence has a big role to play. While it cannot replace a talented hacker, it will be able to exploit the data to which it has access to anticipate certain bad practices and types of code that have generated flaws in the past.